Top 10 Best Phishing Tools for Advanced Protection (2025)

Phishing is one of the most common and successful attack methods used by cybercriminals to steal private information from unsuspecting victims. In these attacks, attackers try to trick users into providing their personal and private information by sending them fraudulent emails, fake site links, or messages that appear to be legitimate. To combat these attacks, experts have developed a variety of tools and techniques to help organizations identify and prevent these attacks. In this article, we’ll be taking a look at the top 10 best phishing tools and free phishing gimmicks of the year that can help you boost your cybersecurity and keep your data safe.
Table of Contents
Best Phishing Tools For Corporates
Now we will take a look into the top 10 best tools that are used for such attacks. Most of these tools are open-source which means they are free to download. There is a wide range of tools in the market but these tools are considered as the top 10 best phishing app due to their wide range of features, flexibility, and effectiveness. Though these are free to download and use, one must know that the use of these tools in a negative manner or with efforts to steal sensitive data from the company or any individual is illegal and punishable by law.
1. PhishGrid
PhishGrid is a web-based online phishing simulation platform that allows you to create phishing campaigns and run phishing campaigns within minutes.
It has a user-friendly framework that allows users to combine attack simulation with awareness education with a feature that redirects phished users to a page with awareness content. Users are free to select from a wide range of awareness content found on the platform and also can create their own.
The dashboard also provides clear insights on the phishing rate of organizations including user clicks, views, most vulnerable users, etc.

And the best part – it’s free. You can Sign Up here and start using it.
Features:
- Large number of templates
- Integrated with AI
- Large number of Awareness content
- Up-to date contents
2. KnowBe4 Security Awareness Training
KnowBe4 is the world’s largest integrated security awareness training and simulated phishing platform with over 65,000 customers. The KnowBe4 platform is user-friendly intuitive, and powerful. Multi-language support for the Admin Console and end-user localization options deliver a more immersive learning experience to your users from start to finish.
With the optional customization features to enable gamification, users can compete against their peers on leaderboards and earn badges while learning how to keep their organization safe from cyber attacks.
It also provides automated training campaigns with scheduled reminder emails.

Pros
3. Hoxhunt
Hoxhunt represents a Human Risk Management solution that surpasses traditional security awareness by actively promoting behavioral transformation, resulting in a quantifiable reduction in risk.
Leveraging a blend of artificial intelligence and behavioral science, Hoxhunt tailors personalized micro-training encounters that users find engaging.
This approach empowers employees to identify and report sophisticated attacks. Moreover, Hoxhunt streamlines incident resolution through automated processes, enabling operational teams to act swiftly despite resource constraints.

4. MetaCompliance Security Awareness Training
MetaCompliance security awareness training platform serves as a comprehensive resource for cyber security awareness, compliance, and policy obligations. MetaCompliance offers customers a fully integrated and multi-lingual suite of cyber security awareness training and compliance capabilities, encompassing policy management, privacy, eLearning, mimic attacks, and risk management.
Key service features include forms-based authentication to accommodate non-network users, hosting on Microsoft Azure, single sign-on functionality, remote accessibility, and personalized security awareness training content.
The benefits of their service are numerous. It allows access at any time, from anywhere, and on any device, fostering user engagement in compliance practices. Additionally, it empowers non-network users to complete compliance training, resulting in time and cost savings for compliance initiatives.

5. Proofpoint Security Awareness Training
Proofpoint Security Awareness employs a threat intelligence-driven approach to education, aimed at mitigating people-related risks, enhancing overall security, and facilitating compliance initiatives. Their Security Awareness solution is rooted in established learning principles, fostering behavioral change, enhancing knowledge retention, and cultivating enduring security practices that extend into individuals’ personal lives.
Knowledge and culture assessments to precisely gauge individuals’ knowledge, identify knowledge gaps, and assess their security attitudes.
Attack simulation layouts, modeled after real-world attacks, equip learners with the skills to counter imminent threats.
An adaptive learning framework encompassing a comprehensive library of over 600 learning components. These components can be tailored to align with users’ preferred learning styles (interactive, gamified, micro or nano content), their roles, competency levels, or specific domain-knowledge requirements. The modules are accessible in over 40 languages and can be customized to reflect the organization’s identity.
The PhishAlarm email report button is seamlessly integrated into their CLEAR infrastructure, streamlining security response and reinforcing positive behavior change when users report suspicious emails.
The CISO Dashboard and pre-configured reports, enable administrators to benchmark their progress against industry peers and effortlessly convey the program’s impact to their executive team.

6. Arctic Wolf
Arctic Wolf Security Awareness Training offers a multifaceted approach to cybersecurity education, focusing on both general security awareness and tailored, organization-specific content.
Arctic Wolf employs various engaging learning methods, including videos, simulations, quizzes, and hands-on exercises. These interactive elements help learners understand complex security concepts and retain crucial information effectively.
One of the standout features of Arctic Wolf’s program is its phishing simulations. These mimic real-world attacks, allowing employees to experience the threat firsthand in a safe environment. By tracking how employees respond to these simulated attacks, organizations can identify vulnerable areas that require further training and support.
The program provides organizations with detailed reports and analytics on employee participation and performance in training components and simulations. These insights help management assess the overall security awareness of the workforce and target areas where improvement is needed.

7. NINJIO Security Awareness
Through engaging training, individualized testing, and insightful reporting, NINJIO reduces human-based cybersecurity risk. It focuses on the latest attack vectors to build employee knowledge and the behavioral science behind human engineering to sharpen users’ intuition.
NINJIO Risk Algorithm identifies users’ social engineering vulnerabilities based on simulation data and informs content delivery to provide a personalized experience that changes individual behavior.

8. SoSafe
People-centered cyber security awareness training and human risk management. SoSafe’s GDPR-compliant awareness workshops enable firms to develop a security culture and mitigate risk.
SoSafe delivers engaging individualized learning experiences and sophisticated attack simulations powered by behavioral science and clever algorithms, transforming employees into active assets against online attacks.

9. SANS Security Awareness Training
SANS Institute offers a wide range of products that address many aspects of security awareness and education.
SANS provides useful resources and tools for end users and phishing simulation. They also offer short-form technical material and brandable corporate communications, allowing you to use SANS’ expertise in human risk management.
SANS Institute further aids your security efforts by offering workforce assessments. These assessments help identify vulnerabilities in your organization’s knowledge and readiness.

10. Hacker Rangers Security Awareness
Hacker Rangers introduces itself as the world’s pioneer in completely gamified security awareness training platforms. Gamification’s distinct methodology dramatically improves the learning experience for employees, making it not only instructional but also enjoyable. Within this gamified ecosystem, Hacker Rangers offers a variety of entertaining elements, such as leaderboards, badges, and ranks, that businesses can use to turn the adoption of safe behaviors into a real-life, competitive game.
It involves offering short, focused, and bite-sized lessons, allowing employees to easily grasp crucial concepts related to identifying fake messages, social manipulation tactics, and other vulnerabilities. Their comprehensive range of educational materials includes animated and subtitled videos, handouts, quizzes, and much more, ensuring a diverse and effective learning experience.

Best Tool for Phishing Attack (Ethical Hacking)(2025)
Now we will look into the tools for phishing attacks which are used by ethical hackers to execute phishing campaigns.
1. Simple Phishing Toolkit
Simple Phishing Toolkit is a web-based framework that allows you to create campaigns quickly and easily.
It is an open source tool that provides an opportunity to combine phishing tests with security awareness education, with a feature that (optionally) directs phished users to a page with an awareness education video.
It is a free tool that is straightforward to use and comes with a user-friendly web interface that makes it easy to create and manage campaigns. This can help in running free phishing security test which mimics real-world phishing.

2. King Phisher
King Phisher is designed for testing and promoting user awareness by simulating real-world attacks.
This tool provides many features, including the ability to run multiple campaigns simultaneously, geo-location of phished users, web cloning capabilities, and more.
King Fisher server is only supported on Linux, with additional installation and configuration steps required depending on flavor and existing configuration.
According to the official documentation, it also supports sending messages with embedded images and determining when emails are opened with a tracking image.

3. Social-Engineer Toolkit (SET)
Social-Engineer Toolkit is an open source penetration testing framework designed for social engineering.
SET includes several tools and modules that can be used to simulate various social engineering attacks, including spear-phishing, log-in details harvesting, new phishing types, and more.
SET is an excellent tool for security professionals and penetration testers who want to test their organization’s security against such attacks.

The Setoolkit is built on Python and integrates several well-known security tools to create a comprehensive platform for performing such attacks.
4. Gophish
Gophish is an open-source toolkit designed for businesses and penetration testers. Gophish is a widely used open source phishing campaign tool.
This tool allows you to create and run campaigns quickly and easily, with customizable email skeletons and landing pages.
Gophish also comes with a powerful reporting engine that provides detailed insights into your campaigns’ performance, allowing you to identify areas for improvement and track your progress over time.
The framework provides a web-based user interface that allows users to design and customize emails and landing pages, track responses and clicks, and measure the success of the campaign.

The framework provides a web-based user interface that allows users to design and customize emails and landing pages, track responses and clicks, and measure the success of the campaign.
5. Evilginx2
Evilginx2 is a man-in-the-middle attack framework used for phishing login details along with session cookies.
This tool is particularly useful for targeting users of online services such as Gmail, Yahoo, and Facebook.
Evilginx2 is relatively easy to use, and it comes with a variety of features that allow you to customize your campaigns to maximize their effectiveness.
It is designed to bypass two-factor authentication (2FA) and other advanced security measures by intercepting user login details and session cookies.

It uses a technique called “real-time phishing” to trick users into entering their login details on a fake login page that is virtually identical to the legitimate website.
The user is then immediately redirected to the legitimate website, making it difficult for the user to detect that they have been phished.
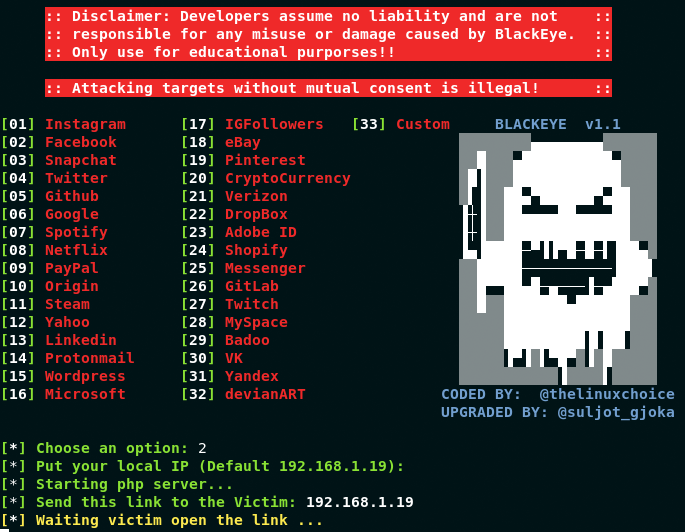
6. Blackeye
Blackeye tool is an open-source tool that is designed to automate the creation of classic phishing pages and capture user login details. Blackeye has the same functionality as zphisher and can be considered as a zphisher alternative.
Black eye phishing tool functions by generating a fake login page that imitates the appearance and functionality of the target website or service, tricking the user into providing their login details.
The user’s entered login details are then recorded by the tool and stored on the attacker’s machine for future use.
7. Hidden Eye
Hidden Eye is a versatile tool designed to execute a range of online attacks targeting user accounts. With its extensive features, it can be employed for keylogging (keystroke logging), phishing, information gathering, social engineering, and more.

The seamless integration of its functional components gives Hidden Eye a significant advantage when attacking accounts. Through brute force attacks, it can efficiently access a user’s personal information. Hidden Eye is capable of easily cracking passwords and gathering additional personal data from the victim.
8. Modlishka
Modlishka is a powerful and flexible reverse proxy tool designed for advanced attacks. and is designed to automate the creation of phishing pages and capture user login details.

It works by creating a reverse proxy between the victim and the target website, allowing it to intercept and modify the traffic between the two.
The tool can automatically generate fake pages that mimic the appearance and functionality of the target website, and then capture user login details as they are entered into the fake login page.
9. Phishing Frenzy
Phishing Frenzy is an open-source phishing framework designed for penetration testers and security professionals.
It is a web-based free phishing simulator that empowers users to create and execute phishing campaigns against various targets.

The tool comes equipped with numerous phishing examples and scenarios that can be personalized to fit specific requirements.
This tool integrates with third-party services to automate the delivery of phishing emails.
The tool is highly customizable and provides a range of options for configuring phishing emails, landing pages, and payloads.
10. Wifiphisher
Wifiphisher is a security tool designed for testing and simulating wireless phishing attacks. It is also one of the phishing tool in kali linux.
It operates by setting up a bogus access point that masquerades as a genuine wireless network.
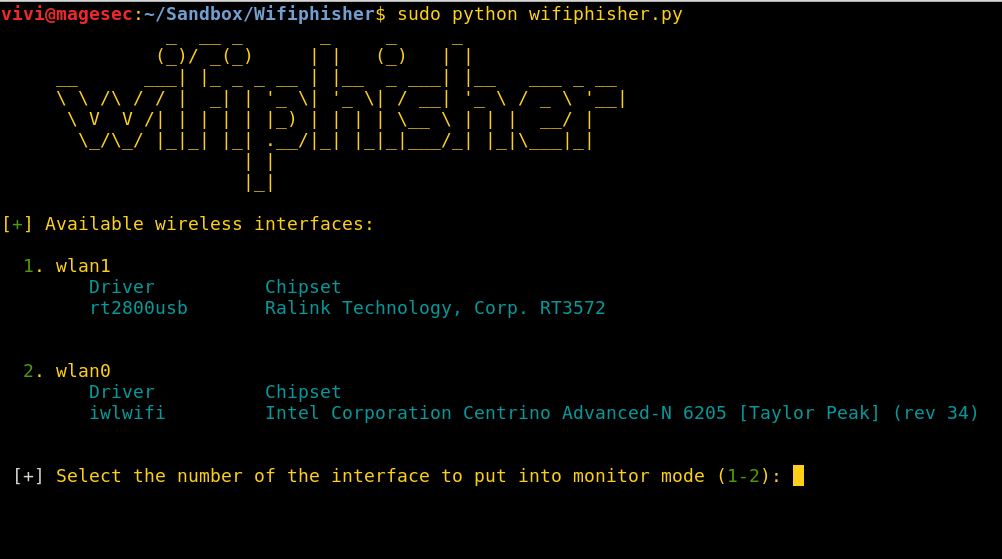
Once a user connects to this counterfeit network, Wifiphisher deceives them into entering their login details or other confidential information on a fabricated login page.
This data is then gathered by the tool, which can be exploited by attackers to unlawfully access the victim’s accounts or systems.
Few Other Phishing tools
Zphisher
Zphisher is an open source phishing platform that is designed to automate various types of phishing attacks.
It streamlines the process of generating and executing attacks and can be leveraged to replicate diverse kinds of attacks such as credential harvesting, spear-phishing, and clone phishing.
The tool offers an assortment of phishing layouts and scenarios that can be personalized to correspond with the targeted website or service.

INFOSEC IQ (IQ PhisSim)
IQ PhisSim is a phishing simulation platform developed by INFOSEC
Users can create unique phishing campaigns using IQ PhishSim’s vast phishing layout library to train staff members on how to counter the most hazardous threats they now face.
To help organizations stay on top of evolving dangers, new layouts are uploaded to the collection every week.
An employee who clicks on a fake phishing link is immediately taken to a quick training module that explains what went wrong, ensuring that training is given as soon as the error is discovered.

Android Phishing Protection Apps
Although there are no mobile phishing apps in the market to execute phishing simulation attacks, there are few phishing apps android to protect you against the phishing websites. We will look into few below:
LinkWall: Check & Analyze Link
LinkWall is a mobile app to check and scan links for online security threats and protect against phishing scam websites.
Key Features of LinkWall:
🔎 Incognito Mode: Go undercover with our Integrated Incognito mode. Browse without leaving a trace, ensuring your online privacy is intact.
🤖 Web Scanner: Seamlessly check all links in the background, safeguarding you from lurking threats on compatible browsers blocking harmful websites.
📸 QR Scanner Security: Easily scan QR codes, ensuring the linked content is genuine and safe to explore.
🕵️♀️ Link Scanning: Every link you access gets an automatic safety check, keeping you shielded from scams, phishing, and harmful sites.
Netcraft Phishing Protection
Netcraft is one of the best anti phishing tools that protects you from phishing and web-based malware attacks on your mobile device. The app will block all known attacks whilst you browse the web.
Features:
✔ Block phishing and web-based malware attacks whilst browsing the web
✔ Report phishing attacks to help protect others and climb the Netcraft leaderboard
✔ View your block history and stats to see how Netcraft has protected you
Conclusion
In conclusion, there are numerous tools available that can be used by attackers to carry out such attacks. These tools automate and simplify the process of creating and launching phishing campaigns, and can be used to deceive users into divulging sensitive information. The top 10 best phishing tools, including PhishGrid, Evilginx2, Gophish, Modlishka, Blackeye, Wifiphisher, Phishing Frenzy, SET, Zphisher, SocialFish, and ShellPhish, offer a range of features and functionalities that can be customized to match the targeted website or service. It is important for individuals and organizations to be aware of these tools and to take proactive measures to protect themselves against phishing attacks, such as using strong passwords, enabling two-factor authentication, and implementing anti-phishing technologies.
You can also run attack simulations on your own by following our guide on how to design a phishing attack simulation. Now that you know about such attacks and how it works you can be more vigilant to avoid such devastating loss.