5 Examples of Dangerous WhatsApp Phishing Attacks

With over 2 billion users who use WhatsApp, WhatsApp has undoubtedly become an integral part of our everyday communication. But as with any popular platform, it also became a fertile ground for cybercriminals, leading to a surge in WhatsApp attacks. Its use in the workplace has increased significantly in recent years as it is easy to send messages and whatsapp provides safety features such as end-to-end encryption on both mobile and PC as well as on WhatsApp web.
What is a WhatsApp Phishing Attack?
Attacks on such platforms involve scams where fraudsters fool users into giving up sensitive details like passwords, credit card numbers, or bank details.
They may impersonate a trusted entity or create a sense of urgency, preying on unsuspecting users.
The techniques used to be relatively straightforward, making them easier to detect. However, starting in 2019, a more sophisticated approach has emerged, enabling phishers to gain control over your account.
As a result, the success rate of these scams has significantly risen.

The techniques used to be relatively straightforward, making them easier to detect. However, starting in 2019, a more sophisticated approach has emerged, enabling phishers to gain control over your account.
As a result, the success rate of these scams has significantly risen.
How does the WhatsApp phishing scam work?
\Attackers use common social engineering techniques and tactics to trap users into divulging personal or corporate information.
Attackers impersonate the CEO or any trusted member and impose a sense of emergency while sending such messages. In recent times there has been an increase in unknown Whatsapp calls with such motives.
Attackers craft different types of messages such as Mom and Dad requesting money, mimicking friends for verification code scams or financial assistance, etc.
Most of the time the users fall victim to such attacks as they tend to be messages from trusted parties.
Why are WhatsApp Users Targeted?
Given its user base and the trust people place in the platform, it’s no surprise that this chat platform has become a favorite tool for fraudsters. Cybercriminals go where the numbers are, and the platform provides an abundant pool of potential victims.
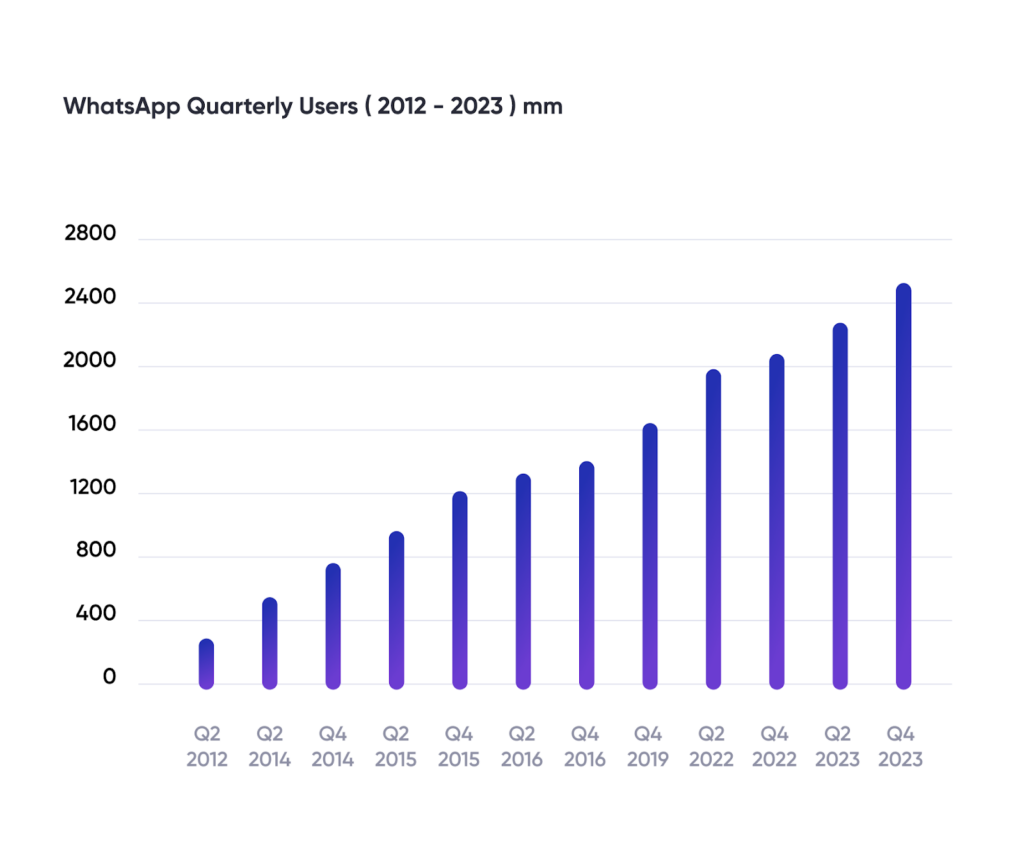
Due to its widespread usage, it has become increasingly favored by fraudsters.
This popularity is precisely why the Fraud Help Desk now receives approximately one thousand reports each month regarding fraudulent activities on the platform.
Common Techniques and Tactics
From fake messages and missed calls to mimic users by hacking their accounts, the ingenuity of these scams is often shocking. They quickly adapt their strategies, continuously revising their modus operandi to stay a step ahead.
The attackers often use a very simple message such as a message from a manager or employee asking to purchase gift cards on an urgent basis as they are in an important meeting.
The attackers also know the name and other details of the employee/user they are trying to trick which makes such attempts more successful.
5 Shocking Examples of WhatsApp Attacks
These attacks are a type of cybercrime where attackers use various techniques to fool users into revealing their personal information, such as login credentials, financial details, or other sensitive details. These attacks exploit the trust and popularity of the platform to deceive unsuspecting users. Here are five shocking examples of WhatsApp attacks:
#A. Through Missed Calls
In recent times, users have been inundated with missed video and voice calls from various country codes. Answering or returning these calls can result in such attacks.
1. How is it carried out?
Once the missed call is made, the attackers typically send a message to the target claiming that they have dialed the wrong number or expressing urgency to communicate about an important matter.
They may pose as a friend, a family member, or even a representative from a trusted organization.

The message often includes a request to share a code or personal details, such as account credentials or financial information. The scammer preys on the target’s curiosity or concern, hoping that they will unknowingly provide the requested information.
If the target falls for the scam and shares the requested information, the attackers can gain unauthorized access to their WhatsApp account, using it for malicious purposes like spreading spam, scamming contacts, or extracting more sensitive details.
2. How to Prevent falling for such scams?
- If the person is claiming to be any of your trusted individuals call back and verify their identity before sharing any information.
- If the message is a financial matter and if the person is causing a sense of urgency in you, take some time and call back the individual to confirm the identity before moving on to the transaction. Do not make any transaction without verification if it’s requested over a message.
#B. Fake Message Lure – Job Offers
Scammers often craft messages designed to fool users into divulging personal information. These fake messages can be alarmingly convincing, asking you to input credentials or verify account details.
These messages are mostly in the form of WFH (work from home) or any type of offer that requests you to visit a site for the application or asks for your personal information.
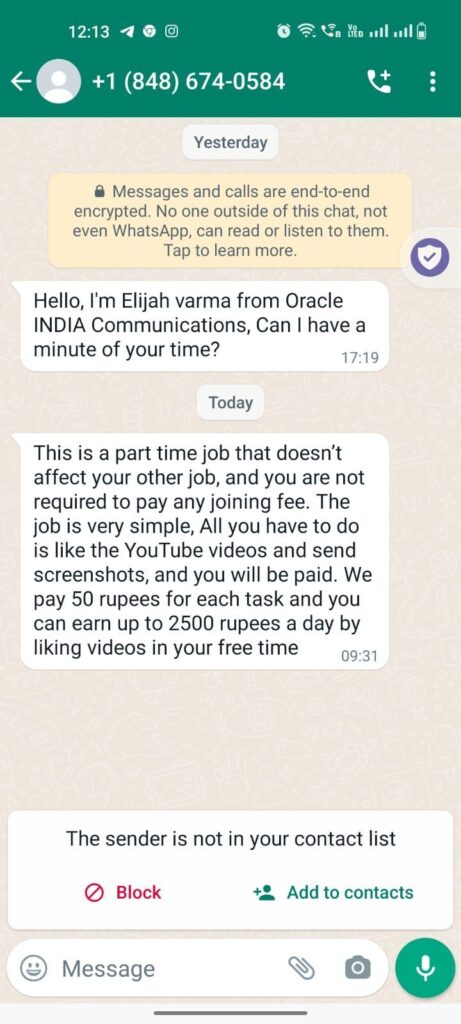
Scammers are also offering Rs50 for liking a video or photo they share over WhatsApp messages. These scammers use social media platforms such as WhatsApp, LinkedIn, and Facebook to entice their victims and earn up to 5,000rs per day.
For providing the payment they frequently ask for personal information and also ask for payment in exchange for a job which does not exist.
1. How is it carried out?
This scam begins by sending victims a message informing them that they have a job with limited slots and in order to reserve a slot you must respond to the message.
Once you respond and ask for Job details, the scammer tells you it’s a simple job and all you have to do is like YouTube videos and send a screenshot of the like and you will be paid 50 per like.
Some scammers even provide 100 – 150 rs at the beginning to have the victim hooked.
Once you like the video and send them the screenshot of the tasks provided the scam moves to phase 2.
In phase 2, scammers act as if there are some difficulties in transferring the amount and will ask you to download an app for easy transfer.
This app contains malware or trojan and acts as an entry point to your mobile and your personal information.
The scammer will then request you to send 1rs for the payment gateway verification after which they will get access to all your OTP’s, Emails, and even your bank information.
2. How to Prevent falling for such scams?
- Do not reply to any messages from suspicious numbers offering Jobs or any other type of offers. It is advised to block such numbers right away.
- Do not download any app that seems suspicious or that an unknown individual suggests.
#C. Social Media Trap
Attackers also use social media platforms like Facebook or Instagram to launch their attacks. They create fake accounts and post deceptive messages luring users into traps with enticing offers or threatening account closures.
#D. Account Impersonation / Hacked Account
The most prevalent scam at the moment is WhatsApp impersonation, where the attacker pretends to be someone you know or trust. This can be your parents, friends, or mostly colleagues of the company you work at or even the CEO of a company.
In this type of attack, attackers gather information on the CEO or the target they are going to impersonate via LinkedIn or any other social media.
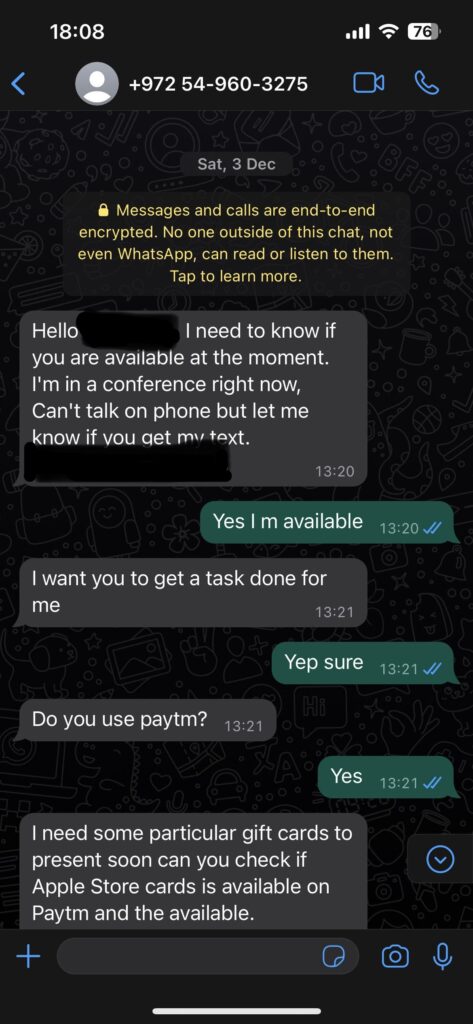
The attackers then use their names and pictures and send messages to the victim.
The messages will be well crafted and will have a sense of emergency to make the victim ignore to fact-check such messages.
Most of the time these messages will have financial gains or personal information leaks and have a high rate of success as they appear from a trusted source.
1. How to Prevent falling for such scams?
- If you get such messages, firstly call back and confirm if the person is who he is claiming to be or request a voice note from the person to verify the identity.
#E. Two-Step Verification Scam
In a more sophisticated scam, attackers set up two-step verification on the victim’s account. The user might be locked out of their account for days, losing control over their data.
In this type of attack, the victim receives messages from a suspicious number that contains a code.
Then the unknown number will apologize for sending their Verification code to your number and press you to share the code.
Once you share the code your account will be taken over by the attacker.
1. How to Prevent falling for such scams?
- WhatsApp sends these codes as push notifications when you register your phone number on the app. This could happen if someone mistyped your number or is trying to take over your account.
- If you get a text message with an unexpected code, delete it. Block any WhatsApp user that asks you to send them a code or PIN. Finally, turn on two-step verification if you receive multiple one-time codes out of the blue.
How To Protecting Yourself
Protecting yourself from WhatsApp attacks is crucial to safeguard your personal information and prevent unauthorized access to your account. Here is a brief introduction on how to stay safe:
#1. Call to Confirm
Always be wary of any message that induces panic, offers unrealistic deals, or asks for personal information. Unusual urgency or pressure is often a sign of such an attempt. Always call and verify who is on the other side before sharing any information.
#2. Be wary of urgent money requests
Scammers always cause of sense of emergency on money requests. Always question urgent requests for money
#3. Report to Whatsapp
Report any suspicious activity to WhatsApp right away. They can work on shutting down these fraudulent accounts and ensure other users are not impacted.
#4. Never answer a WhatsApp call from an Unknown Number
Attackers call random users from mobile numbers obtained from possible data leaks using international numbers to pose fake job offers etc. It is advised not to attend any unknown call over WhatsApp and block such numbers immediately.
#5. Change Whatsapp privacy settings
Change your privacy settings to view your last seen, profile picture, and to only contacts or nobody.
#6. Set up 2FA
Two-factor authentication helps to improve the security of any online account, not just your WhatsApp account.
Setting this up ensures an additional layer of protection when you log into an app. A one-time code is sent to your phone, email, or authentication app before you can log in to WhatsApp.
Conclusion
With technology becoming more embedded in our lives, cybersecurity awareness is crucial. Understanding the tactics employed by attackers can protect us and our sensitive data from falling into the wrong hands. With increasing WhatsApp scams it is best to know the steps that can protect you from losing sensitive data to financial information.